In the mid-1980s, the network technologies that had emerged had been created with a variety of different hardware and software implementations. Each company that created network hardware and software used its own company standards. These individual standards were developed because of competition with other companies. Consequently, many of the new network technologies were incompatible with each other. It became increasingly difficult for networks that used different specifications to communicate with each other. This often required the old network equipment to be removed to implement the new equipment.
One early solution was the creation of local-area network (LAN) standards. Because LAN standards provided an open set of guidelines for creating network hardware and software, the equipment from different companies could then become compatible. This allowed for stability in LAN implementation.
In a LAN system, each department of the company is a kind of electronic island. As the use of computers in businesses grew, it soon became obvious that even LANs were not sufficient.
What was needed was a way for information to move efficiently and quickly, not only within a company, but also from one business to another. The solution was the creation of metropolitan-area networks (MANs) and wide-area networks (WANs). Because WANs could connect user networks over large geographic areas, it was possible for businesses to communicate with each other across great distances. Figure summarizes the relative sizes of LANs and WANs.
Network history
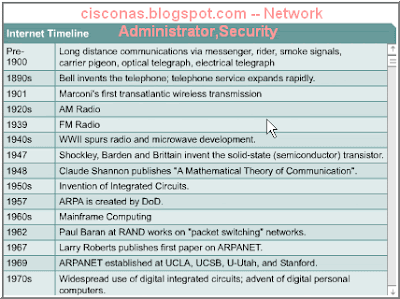
The history of computer networking is complex. It has involved many people from all over the world over the past 35 years. Presented here is a simplified view of how the Internet evolved. The processes of invention and commercialization are far more complicated, but it is helpful to look at the fundamental development.
In the 1940s computers were large electromechanical devices that were prone to failure. In 1947 the invention of a semiconductor transistor opened up many possibilities for making smaller, more reliable computers. In the 1950s mainframe computers, which were run by punched card programs, began to be used by large institutions. In the late 1950s the integrated circuit that combined several, then many, and now millions, of transistors on one small piece of semiconductor was invented. Through the 1960s mainframes with terminals were commonplace, and integrated circuits were widely used.
In the late 1960s and 1970s, smaller computers, called minicomputers came into existence. However, these minicomputers were still very large by modern standards. In 1977 the Apple Computer Company introduced the microcomputer, also known as the personal computer. In 1981 IBM introduced its first personal computer. The user-friendly Mac, the open-architecture IBM PC, and the further micro-miniaturization of integrated circuits led to widespread use of personal computers in homes and businesses.
In the mid-1980s users with stand-alone computers started to share files using modems to connect to other computers. This was referred to as point-to-point, or dial-up communication. This concept was expanded by the use of computers that were the central point of communication in a dial-up connection. These computers were called bulletin boards. Users would connect to the bulletin boards, leave and pick up messages, as well as upload and download files. The drawback to this type of system was that there was very little direct communication and then only with those who knew about the bulletin board. Another limitation was that the bulletin board computer required one modem per connection. If five people connected simultaneously it would require five modems connected to five separate phone lines. As the number of people who wanted to use the system grew, the system was not able to handle the demand. For example, imagine if 500 people wanted to connect at the same time. Starting in the 1960s and continuing through the 70s, 80s, and 90s, the Department of Defense (DoD) developed large, reliable, wide-area networks (WANs) for military and scientific reasons. This technology was different from the point-to-point communication used in bulletin boards. It allowed multiple computers to be connected together using many different paths. The network itself would determine how to move data from one computer to another. Instead of only being able to communicate with one other computer at a time, many computers could be reached using the same connection. The DoDs WAN eventually became the Internet.
Networking devices

| Equipment that connects directly to a network segment is referred to as a device. These devices are broken up into two classifications. The first classification is end-user devices. End-user devices include computers, printers, scanners, and other devices that provide services directly to the user. The second classification is network devices. Network devices include all the devices that connect the end-user devices together to allow them to communicate. End-user devices that provide users with a connection to the network are also referred to as hosts. These devices allow users to share, create, and obtain information. The host devices can exist without a network, but without the network the host capabilities are greatly reduced. Host devices are physically connected to the network media using a network interface card (NIC). They use this connection to perform the tasks of sending e-mails, printing reports, scanning pictures, or accessing databases. A NIC is a printed circuit board that fits into the expansion slot of a bus on a computer motherboard, or it can be a peripheral device. It is also called a network adapter. Laptop or notebook computer NICs are usually the size of a PCMCIA card. Each individual NIC carries a unique code, called a Media Access Control (MAC) address. This address is used to control data communication for the host on the network. More about the MAC address will be covered later. As the name implies, the NIC controls host access to the medium. There are no standardized symbols for end-user devices in the networking industry. They appear similar to the real devices to allow for quick recognition. Network devices provide transport for the data that needs to be transferred between end-user devices. Network devices provide extension of cable connections, concentration of connections, conversion of data formats, and management of data transfers. Examples of devices that perform these functions are repeaters, hubs, bridges, switches, and routers. All of the network devices mentioned here are covered in depth later in the course. For now, a brief overview of networking devices will be provided. A repeater is a network device used to regenerate a signal. Repeaters regenerate analog or digital signals distorted by transmission loss due to attenuation. A repeater does not perform intelligent routing like a bridge or router. Hubs concentrate connections. In other words, they take a group of hosts and allow the network to see them as a single unit. This is done passively, without any other effect on the data transmission. Active hubs not only concentrate hosts, but they also regenerate signals. Bridges convert network transmission data formats as well as perform basic data transmission management. Bridges, as the name implies, provide connections between LANs. Not only do bridges connect LANs, but they also perform a check on the data to determine whether it should cross the bridge or not. This makes each part of the network more efficient. Workgroup switches add more intelligence to data transfer management. Not only can they determine whether data should remain on a LAN or not, but they can transfer the data only to the connection that needs that data. Another difference between a bridge and switch is that a switch does not convert data transmission formats. Routers have all the capabilities listed above. Routers can regenerate signals, concentrate multiple connections, convert data transmission formats, and manage data transfers. They can also connect to a WAN, which allows them to connect LANs that are separated by great distances. None of the other devices can provide this type of connection. Network topology 
Network topology defines the structure of the network. One part of the topology definition is the physical topology, which is the actual layout of the wire or media. The other part is the logical topology, which defines how the media is accessed by the hosts for sending data. The physical topologies that are commonly used are as follows: - A bus topology uses a single backbone cable that is terminated at both ends. All the hosts connect directly to this backbone.
- A ring topology connects one host to the next and the last host to the first. This creates a physical ring of cable.
- A star topology connects all cables to a central point of concentration.
- An extended star topology links individual stars together by connecting the hubs and/or switches. This topology can extend the scope and coverage of the network.
- A hierarchical topology is similar to an extended star. However, instead of linking the hubs and/or switches together, the system is linked to a computer that controls the traffic on the topology.
- A mesh topology is implemented to provide as much protection as possible from interruption of service. The use of a mesh topology in the networked control systems of a nuclear power plant would be an excellent example. As seen in the graphic, each host has its own connections to all other hosts. Although the Internet has multiple paths to any one location, it does not adopt the full mesh topology.
The logical topology of a network is how the hosts communicate across the medium. The two most common types of logical topologies are broadcast and token passing. Broadcast topology simply means that each host sends its data to all other hosts on the network medium. There is no order that the stations must follow to use the network. It is first come, first serve. Ethernet works this way as will be explained later in the course. The second logical topology is token passing. Token passing controls network access by passing an electronic token sequentially to each host. When a host receives the token, that host can send data on the network. If the host has no data to send, it passes the token to the next host and the process repeats itself. Two examples of networks that use token passing are Token Ring and Fiber Distributed Data Interface (FDDI). A variation of Token Ring and FDDI is Arcnet. Arcnet is token passing on a bus topology. The diagram in Figure shows many different topologies connected by network devices. It shows a network of moderate complexity that is typical of a school or a small business. It has many symbols, and it depicts many networking concepts that will take time to learn. Network protocols 
Protocol suites are collections of protocols that enable network communication from one host through the network to another host. A protocol is a formal description of a set of rules and conventions that govern a particular aspect of how devices on a network communicate. Protocols determine the format, timing, sequencing, and error control in data communication. Without protocols, the computer cannot make or rebuild the stream of incoming bits from another computer into the original format. Protocols control all aspects of data communication, which include the following: - How the physical network is built
- How computers connect to the network
- How the data is formatted for transmission
- How that data is sent
- How to deal with errors
These network rules are created and maintained by many different organizations and committees. Included in these groups are the Institute of Electrical and Electronic Engineers (IEEE), American National Standards Institute (ANSI), Telecommunications Industry Association (TIA), Electronic Industries Alliance (EIA) and the International Telecommunications Union (ITU), formerly known as the Comité Consultatif International Téléphonique et Télégraphique (CCITT). Local-area networks (LANs) 
LANs consist of the following components:- Computers
- Network interface cards
- Peripheral devices
- Networking media
- Network devices
LANs make it possible for businesses that use computer technology to locally share files and printers efficiently, and make internal communications possible. A good example of this technology is e-mail. They tie data, local communications, and computing equipment together. Some common LAN technologies are: Wide-area networks (WANs)

| WANs interconnect LANs, which then provide access to computers or file servers in other locations. Because WANs connect user networks over a large geographical area, they make it possible for businesses to communicate across great distances. Using WANs allows computers, printers, and other devices on a LAN to share and be shared with distant locations. WANs provide instant communications across large geographic areas. The ability to send an instant message (IM) to someone anywhere in the world provides the same communication capabilities that used to be only possible if people were in the same physical office. Collaboration software provides access to real-time information and resources that allows meetings to be held remotely, instead of in person. Wide-area networking has also created a new class of workers called telecommuters, people who never have to leave their homes to go to work. WANs are designed to do the following: - Operate over a large geographically separated areas
- Allow users to have real-time communication capabilities with other users
- Provide full-time remote resources connected to local services
- Provide e-mail, World Wide Web, file transfer, and e-commerce services
Some common WAN technologies are: - Modems
- Integrated Services Digital Network (ISDN)
- Digital Subscriber Line (DSL)
- Frame Relay
- US (T) and Europe (E) Carrier Series – T1, E1, T3, E3
- Synchronous Optical Network (SONET)
Metropolitan-area networks (MANs)

A MAN is a network that spans a metropolitan area such as a city or suburban area. A MAN usually consists of two or more LANs in a common geographic area. For example, a bank with multiple branches may utilize a MAN. Typically, a service provider is used to connect two or more LAN sites using private communication lines or optical services. A MAN can also be created using wireless bridge technology by beaming signals across public areas
Storage-area networks (SANs)

A SAN is a dedicated, high-performance network used to move data between servers and storage resources. Because it is a separate, dedicated network, it avoids any traffic conflict between clients and servers. SAN technology allows high-speed server-to-storage, storage-to-storage, or server-to-server connectivity. This method uses a separate network infrastructure that relieves any problems associated with existing network connectivity. SANs offer the following features: - Performance – SANs enable concurrent access of disk or tape arrays by two or more servers at high speeds, providing enhanced system performance.
- Availability – SANs have disaster tolerance built in, because data can be mirrored using a SAN up to 10 kilometers (km) or 6.2 miles away.
- Scalability – Like a LAN/WAN, it can use a variety of technologies. This allows easy relocation of backup data, operations, file migration, and data replication between systems
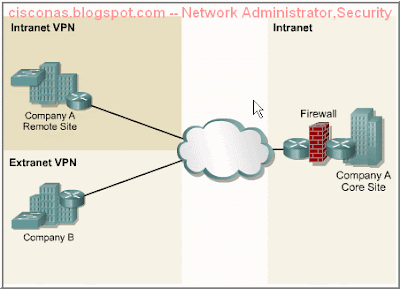
Virtual private network (VPN)
| A VPN is a private network that is constructed within a public network infrastructure such as the global Internet. Using VPN, a telecommuter can access the network of the company headquarters through the Internet by building a secure tunnel between the telecommuter’s PC and a VPN router in the headquarters. |
|
|
|
Benefits of VPNs

Cisco products support the latest in VPN technology. A VPN is a service that offers secure, reliable connectivity over a shared public network infrastructure such as the Internet. VPNs maintain the same security and management policies as a private network. They are the most cost-effective method of establishing a point-to-point connection between remote users and an enterprise customer's network.  The following are the three main types of VPNs: - Access VPNs – Access VPNs provide remote access to a mobile worker and small office/home office (SOHO) to the headquarters of the Intranet or Extranet over a shared infrastructure. Access VPNs use analog, dialup, ISDN, digital subscriber line (DSL), mobile IP, and cable technologies to securely connect mobile users, telecommuters, and branch offices.
- Intranet VPNs – Intranet VPNs link regional and remote offices to the headquarters of the internal network over a shared infrastructure using dedicated connections. Intranet VPNs differ from Extranet VPNs in that they allow access only to the employees of the enterprise.
- Extranet VPNs – Extranet VPNs link business partners to the headquarters of the network over a shared infrastructure using dedicated connections. Extranet VPNs differ from Intranet VPNs in that they allow access to users outside the enterprise.
Intranets and extranets
| One common configuration of a LAN is an Intranet. Intranet Web servers differ from public Web servers in that the public must have the proper permissions and passwords to access the Intranet of an organization. Intranets are designed to permit access by users who have access privileges to the internal LAN of the organization. Within an Intranet, Web servers are installed in the network. Browser technology is used as the common front end to access information such as financial data or graphical, text-based data stored on those servers. Extranets refer to applications and services that are Intranet based, and use extended, secure access to external users or enterprises. This access is usually accomplished through passwords, user IDs, and other application-level security. Therefore, an Extranet is the extension of two or more Intranet strategies with a secure interaction between participant enterprises and their respective intranets. |
|













0 comments:
Post a Comment