
The U.S. Department of Defense (DoD) created the TCP/IP reference model because it wanted a network that could survive any conditions.
In reading about the layers of the TCP/IP model layers, keep in mind the original intent of the Internet. Remembering the intent will help reduce confusion. The TCP/IP model has four layers: the application layer, transport layer, Internet layer, and the network access layer. Some of the layers in the TCP/IP model have the same name as layers in the OSI model. It is critical not to confuse the layer functions of the two models because the layers include different functions in each model.
The present version of TCP/IP was standardized in September of 1981. As shown in Figure ![]() , IPv4 addresses are 32 bits long, written in dotted decimal, and separated by periods. IPv6 addresses are 128 bits long, written in hexadecimal, and separated by colons. Colons separate 16-bit fields. Leading zeros can be omitted in each field as can be seen in the Figure
, IPv4 addresses are 32 bits long, written in dotted decimal, and separated by periods. IPv6 addresses are 128 bits long, written in hexadecimal, and separated by colons. Colons separate 16-bit fields. Leading zeros can be omitted in each field as can be seen in the Figure ![]() where the field :0003: is written :3:. In 1992 the standardization of a new generation of IP, often called IPng, was supported by the Internet Engineering Task Force (IETF). IPng is now known as IPv6. IPv6 has not gained wide implementation, but it has been released by most vendors of networking equipment and will eventually become the dominant standard.
where the field :0003: is written :3:. In 1992 the standardization of a new generation of IP, often called IPng, was supported by the Internet Engineering Task Force (IETF). IPng is now known as IPv6. IPv6 has not gained wide implementation, but it has been released by most vendors of networking equipment and will eventually become the dominant standard.
Application layer
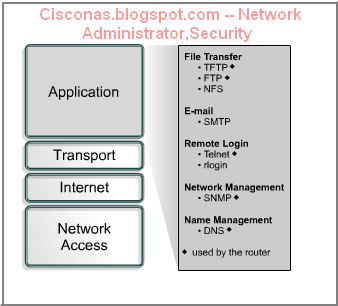
The application layer of the TCP/IP model handles high-level protocols, issues of representation, encoding, and dialog control. The TCP/IP protocol suite combines all application related issues into one layer and assures this data is properly packaged before passing it on to the next layer. TCP/IP includes not only Internet and transport layer specifications, such as IP and TCP, but also specifications for common applications. TCP/IP has protocols to support file transfer, e-mail, and remote login, in addition to the following applications:
- File Transfer Protocol (FTP) – FTP is a reliable, connection-oriented service that uses TCP to transfer files between systems that support FTP. It supports bi-directional binary file and ASCII file transfers.
- Trivial File Transfer Protocol (TFTP) – TFTP is a connectionless service that uses the User Datagram Protocol (UDP). TFTP is used on the router to transfer configuration files and Cisco IOS images, and to transfer files between systems that support TFTP. It is useful in some LANs because it operates faster than FTP in a stable environment.
- Network File System (NFS) – NFS is a distributed file system protocol suite developed by Sun Microsystems that allows file access to a remote storage device such as a hard disk across a network.
- Simple Mail Transfer Protocol (SMTP) – SMTP administers the transmission of e-mail over computer networks. It does not provide support for transmission of data other than plaintext.
- Terminal emulation (Telnet) – Telnet provides the capability to remotely access another computer. It enables a user to log in to an Internet host and execute commands. A Telnet client is referred to as a local host. A Telnet server is referred to as a remote host.
- Simple Network Management Protocol (SNMP) – SNMP is a protocol that provides a way to monitor and control network devices, and to manage configurations, statistics collection, performance, and security.
- Domain Name System (DNS) – DNS is a system used on the Internet for translating names of domains and their publicly advertised network nodes into IP addresses

| The transport layer provides transport services from the source host to the destination host. The transport layer constitutes a logical connection between the endpoints of the network, the sending host and the receiving host. The Internet is often represented by a cloud. The transport layer sends data packets from the sending source to the receiving destination through the cloud. End-to-end control, provided by sliding windows and reliability in sequencing numbers and acknowledgments, is the primary duty of the transport layer when using TCP. The transport layer also defines end-to-end connectivity between host applications. Transport services include all the following services: TCP and UDP
TCP only
The Internet is often represented by a cloud. The transport layer sends data packets from the sending source to the receiving destination through the cloud. |

| The purpose of the Internet layer is to select the best path through the network for packets to travel. The main protocol that functions at this layer is the Internet Protocol (IP). Best path determination and packet switching occur at this layer. The following protocols operate at the TCP/IP Internet layer:
IP performs the following operations:
Finally, as a clarification of terminology, IP is sometimes referred to as an unreliable protocol. This does not mean that IP will not accurately deliver data across a network. Calling IP an unreliable protocol simply means that IP does not perform error checking and correction. That function is handled by upper layer protocols from the transport or application layers. |

| The network access layer is also called the host-to-network layer. Drivers for software applications, modem cards and other devices operate at the network access layer. The network access layer defines the procedures for interfacing with the network hardware and accessing the transmission medium. Modem protocol standards such as Serial Line Internet Protocol (SLIP) and Point-to-Point Protocol (PPP) provide network access through a modem connection. Because of an intricate interplay of hardware, software, and transmission-medium specifications, there are many protocols operating at this layer. This can lead to confusion for users. Most of the recognizable protocols operate at the transport and Internet layers of the TCP/IP model. Network access layer functions include mapping IP addresses to physical hardware addresses and encapsulation of IP packets into frames. Based upon the hardware type and the network interface, the network access layer will define the connection with the physical network media. A good example of network access layer configuration would be to set up a Windows system using a third party NIC. Depending on the version of Windows, the NIC would automatically be detected by the operating system and then the proper drivers would be installed. If this were an older version of Windows, the user would have to specify the network card driver. The card manufacturer supplies these drivers on disks or CD-ROMs |
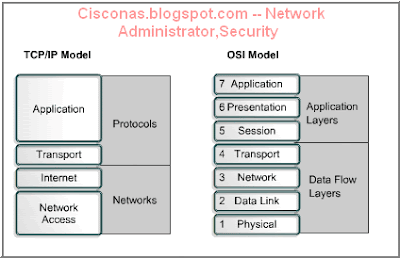
The following is a comparison of the OSI model and the TCP/IP model noting the similarities and differences:
Similarities of the OSI and TCP/IP models:
- Both have layers
- Both have application layers, though they include very different services
- Both have comparable transport and network layers
- Packet-switched, not circuit-switched, technology is assumed
- Networking professionals need to know both models
Differences of the OSI and TCP/IP models:
- TCP/IP combines the presentation and session layer into its application layer
- TCP/IP combines the OSI data link and physical layers into one layer
- TCP/IP appears simpler because it has fewer layers
- TCP/IP transport layer using UDP does not always guarantee reliable delivery of packets as the transport layer in the OSI model does
The Internet is developed by the standards of the TCP/IP protocols. The TCP/IP model gains credibility because of its protocols. In contrast, networks typically are not built on the OSI protocol. The OSI model is used as a guide for understanding the communication process.
Internet architecture
| While the Internet is complex, there are some basic ideas in its operation. In this section the basic architecture of the Internet will be examined. The Internet is a deceptively simple idea, that when repeated on a large scale, enables nearly instantaneous worldwide data communications between anyone, anywhere, at any time. LANs are smaller networks limited in geographic area. Many LANs connected together allow the Internet to function. But LANs have limitations in scale. Although there have been technological advances to improve the speed of communications, such as Metro Optical, Gigabit, and 10-Gigabit Ethernet, distance is still a problem. Focusing on the communication between the source and destination computer and intermediate computers at the application layer is one way to get an overview of the Internet architecture. Placing identical instances of an application on all the computers in the network could ease the delivery of messages across the large network. However, this does not scale well. For new software to function properly, it would require new applications installed on every computer in the network. For new hardware to function properly, it would require modifying the software. Any failure of an intermediate computer or the application of the computer would cause a break in the chain of the messages that are passed. The Internet uses the principle of network layer interconnection. Using the OSI model as an example, the goal is to build the functionality of the network in independent modules. This allows a diversity of LAN technologies at Layers 1 and 2 and a diversity of applications functioning at Layers 5, 6, and 7. The OSI model provides a mechanism where the details of the lower and the upper layers are separated. This allows intermediate networking devices to “relay” traffic without having to bother with the details of the LAN. This leads to the concept of internetworking, or building networks of networks. A network of networks is called an internet, indicated with the lowercase “i”. When referring to the networks that developed from the DoD on which the Worldwide Web (www) runs, the uppercase “I” is used and is called the Internet. Internetworking must be scalable with regard to the number of networks and computers attached. Internetworking must be able to handle the transport of data across vast distances. It must be flexible to account for constant technological innovations. It must be able to adjust to dynamic conditions on the network. And internetworks must be cost-effective. Internetworks must be designed to permit anytime, anywhere, data communications to anyone. Figure Figure One option is for a router to keep a list of all computers and all the paths to them. The router would then decide how to forward data packets based on this reference table. The forwarding is based on the IP address of the destination computer. This option would become difficult as the number of users grows. Scalability is introduced when the router keeps a list of all networks, but leaves the local delivery details to the local physical networks. In this situation, the routers pass messages to other routers. Each router shares information about which networks it is connected to. This builds the routing table. Figure Two computers, anywhere in the world, following certain hardware, software, and protocol specifications, can communicate reliably. Standardization of practices and procedures for moving data across networks has made the Internet possible. |
Cisco Systems, Inc.



0 comments:
Post a Comment